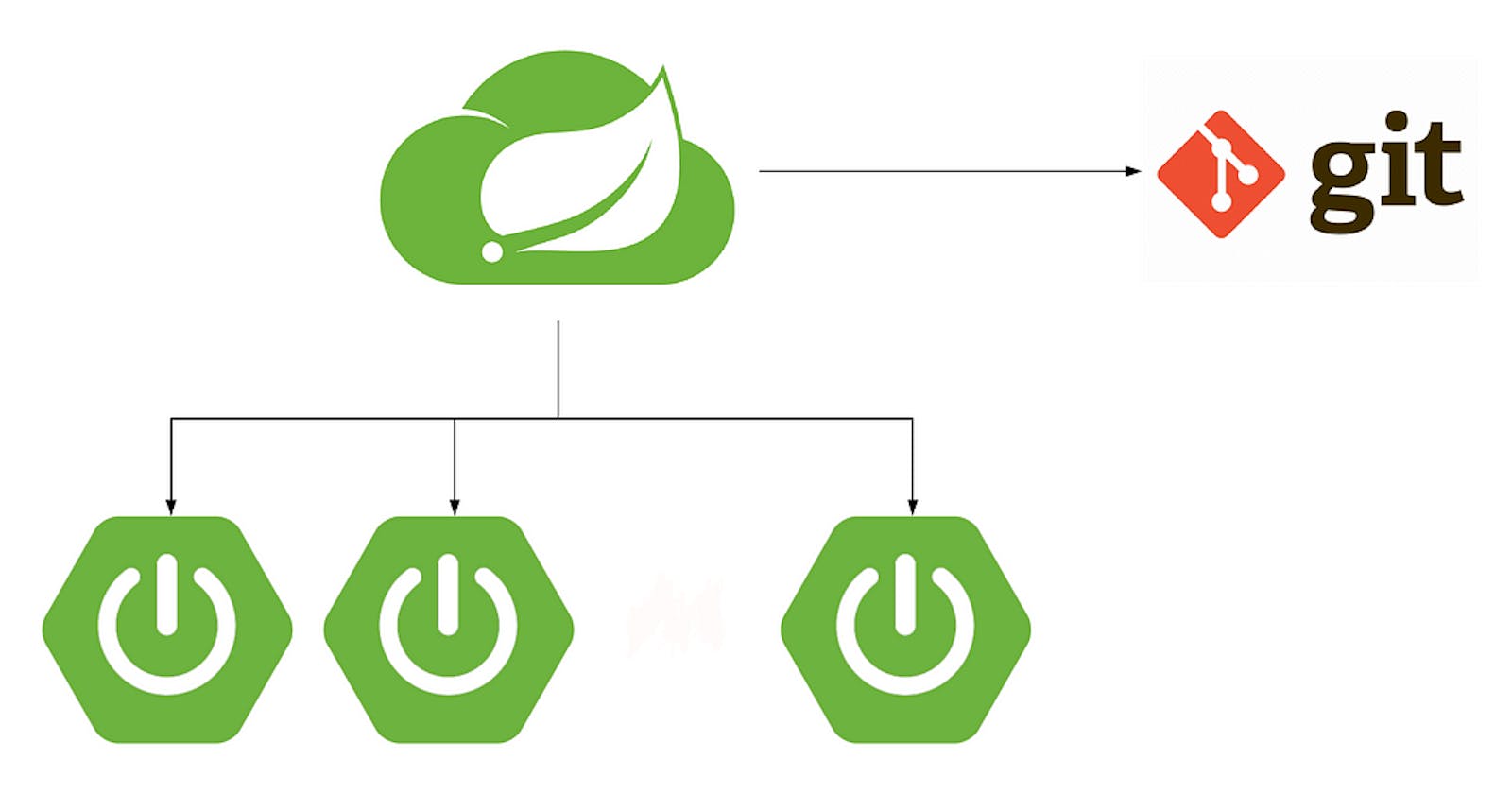
In the world of software development, managing configuration properties efficiently is crucial. One popular method for achieving this is by connecting properties from a GitHub repository. In this article, we’ll explore why this approach is recommended, how to set it up, and considerations for securing sensitive data.
Why Connect Properties from GitHub?
1. Centralized Management
By storing configuration properties in a GitHub repository, you centralize their management. This makes it easier to track changes, collaborate with team members, and maintain consistency across different environments.
2. Version History
GitHub provides a robust version control system. You can view the history of property changes, revert to previous versions, and ensure that your application always uses the correct configuration.
3. Public or Private Repositories
Depending on your requirements, you can keep your GitHub repository public or private. Public repositories allow transparency and collaboration, while private ones enhance security by restricting access.
Implementation Steps
Step 1: Upload Properties Files
Begin by uploading all your configuration properties files to your GitHub repository. These files typically contain key-value pairs for various settings (e.g., database connection details, API keys, etc.).
Step 2: Configure the Config Server
The heart of this approach is the Config Server. In your application.yml (or application.properties), configure the following:
spring:
application:
name: "ConfigServer"
profiles:
active: git
cloud:
config:
server:
git:
uri: "https://github.com/yourusername/your-repo.git"
default-label: main
timeout: 5
clone-on-start: true
force-pull: true
server:
port: 8071
uri: Specify the GitHub repository URL.default-label: Set the default branch (usuallymainormaster).timeout: Define the connection timeout (in seconds).clone-on-start: Clone properties on server startup.force-pull: Override local changes during server restart.
Encryption and Decryption of Properties
Protecting Sensitive Data
Sometimes, you’ll need to store sensitive properties (e.g., passwords, API tokens) in an encrypted format. To prevent unauthorized access, follow these steps:
Generate a Complex Key: Create a strong encryption key. Avoid using common phrases like “123” or “ABC.” Complexity is essential for security.
Use Third-Party Tools: There are third-party tools that can generate secure keys. Explore options like OpenSSL or online key generators.
Configure Encryption in Your Application: In your
application.yml, specify the encryption key:
spring:
encrypt:
key: your-complex-key-here
Remember that the key should be kept confidential. Store it securely and avoid sharing it publicly.
Conclusion
Connecting properties from GitHub streamlines configuration management ensures version control, and allows flexibility in repository visibility. By encrypting sensitive data, you can enhance security and protect your application’s secrets.